Introduction:
The challenge of defending an organization against rapidly evolving, increasingly complex cyberthreats can be considerable. Adversaries continuously adapt and evolve their behavior and toolsets, leverage new vulnerabilities, and misuse everyday IT tools to evade detection and stay one step ahead of security teams.
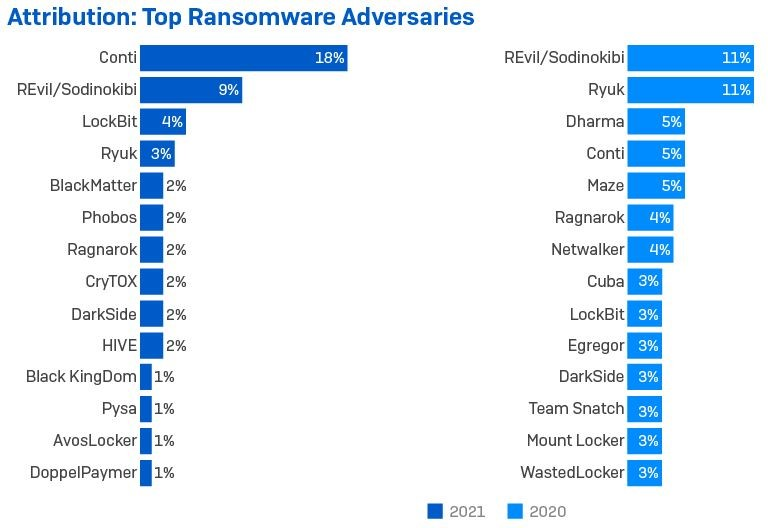
It can be hard for an organization’s IT and security operations professionals to keep up with the latest approaches used by adversaries. This is true particularly when it comes to targeted, active attacks that involve more than one perpetrator, such as an initial access broker (IAB) breaching a target and then selling that access on to a ransomware gang for use in their attack.The Active Adversary Playbook 2022 details the main adversaries, tools, and attack behaviors seen in the wild during 2021 by Sophos’ frontline incident responders. It follows on from the Active Adversary Playbook 2021 and shows how the attack landscape continues to evolve.
The aim is to help security teams understand what adversaries do during attacks and how to spot and defend against such activity on their network.The findings are based on data from incidents investigated by the Sophos Rapid Response team during 2021. Where possible, the data is compared against the incident response findings outlined in the Active Adversary Playbook 2021.
Incident Response Demographics 2021:
The report is based on 144 incidents targeting organizations of all sizes, in a wide range of industry sectors, and located in the U.S., Canada, the U.K., Germany, Italy, Spain, France, Switzerland, Belgium, Netherlands, Austria, the United Arab Emirates, Saudi Arabia, the Philippines, the Bahamas, Angola, and Japan.
The most represented sectors are manufacturing (17% of incident response cases were in this sector) followed by retail (14%), healthcare (13%), IT (9%), construction (8%), and education (6%). Additional profile information can be found in the data tables at the end of this report.
Dashboard: The Anatomy of Active Attacks in 2021:
The report is based on 144 incidents targeting organizations of all sizes, in a wide range of industry sectors, and located in the U.S., Canada, the U.K., Germany, Italy, Spain, France, Switzerland, Belgium, Netherlands, Austria, the United Arab Emirates, Saudi Arabia, the Philippines, the Bahamas, Angola, and Japan.
The most represented sectors are manufacturing (17% of incident response cases were in this sector) followed by retail (14%), healthcare (13%), IT (9%), construction (8%), and education (6%). Additional profile information can be found in the data tables at the end of this report.
The Invisible Intruders:
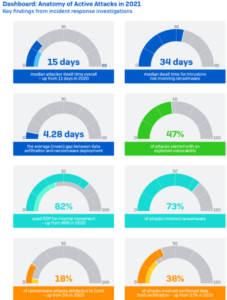
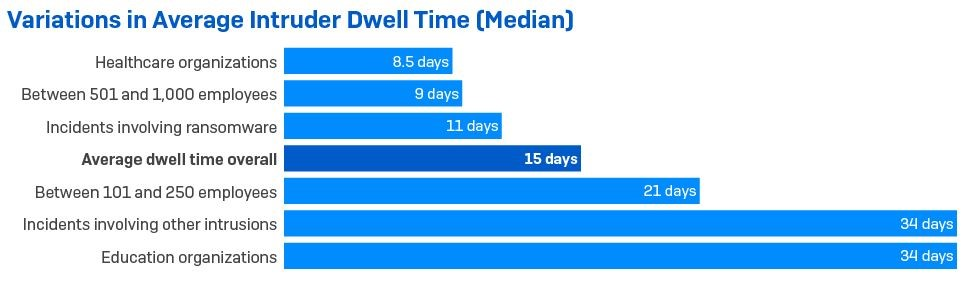
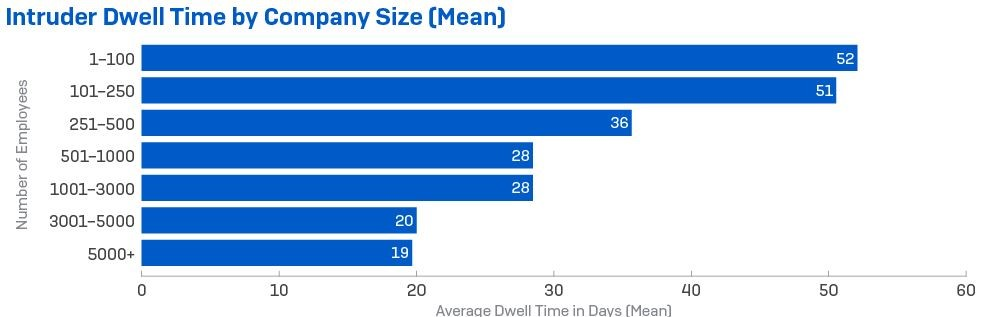
The incident data shows that the median average dwell time increased by about a third between 2020 and 2021, from 11 days to 15. There was considerable variation, with attacks that culminated in ransomware having shorter dwell times, on average around 11 days (down from 18 in 2020), and those involving other intrusions lasting significantly longer, with a median dwell time of 34 days.
The Root Causes of Attacks:
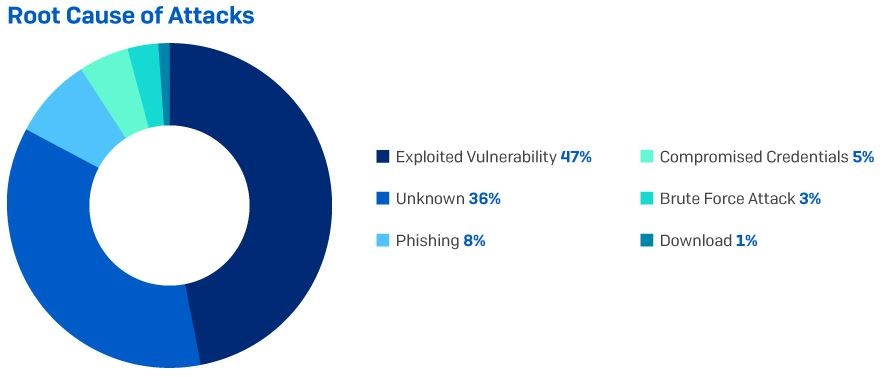
It is not always possible, or easy, to identify the root cause of an attack. Sometimes the attackers have intentionally deleted evidence of their activity and sometimes the IT security team has already wiped or re-imaged compromised machines by the time the responders arrive. Despite this, the evidence shows that among the incidents investigated by Sophos, the exploitation of unpatched vulnerabilities – such as ProxyLogon or ProxyShell – were the root cause for almost half (47%) of cyberincidents investigated in 2021.
The Main Attack Types:
The release of ransomware is often the point at which an attack becomes visible to the IT security team. It is therefore not surprising that 73% of the incidents Sophos responded to in 2021 involved ransomware. Ransomware was also the most prevalent attack type in 2020, at 82% (the higher number likely reflecting the smaller data set). In the case of data exfiltration, accounting for 1% of incidents, the incident responders believe these would probably have unfolded into ransomware attacks but were caught and neutralized in time.
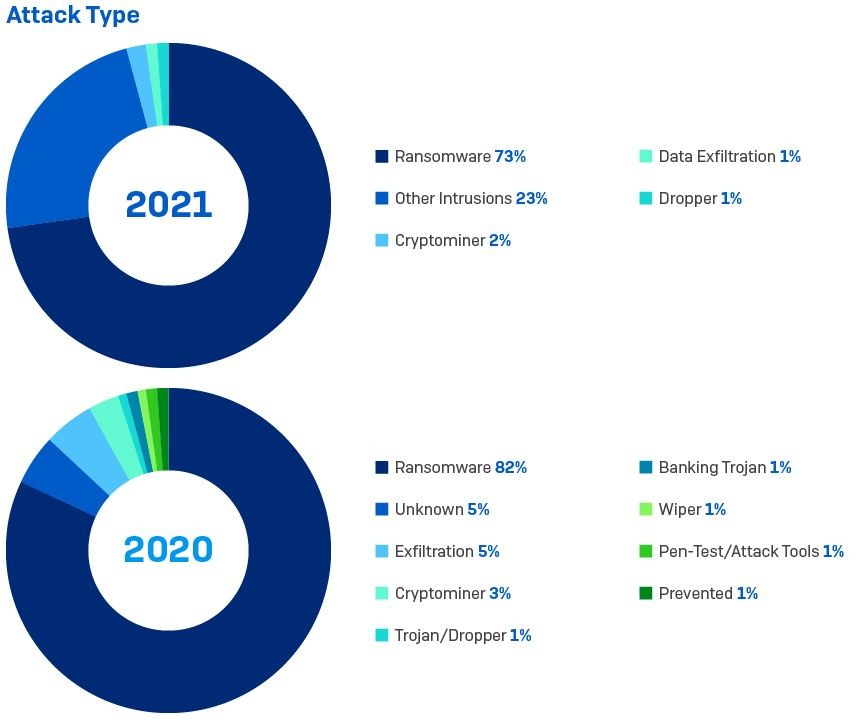
The second most prevalent type of attack uncovered by incident response investigations was the broad category of “other intrusion,” which accounted for 23% of incidents. For the purposes of this report “other intrusions” are defined as intrusions that have not resulted in ransomware or other tracked attack type.
An intrusion is often the result of an exploited unpatched vulnerability, such as ProxyLogon and ProxyShell, but also includes the misuse of remote access services or insecure VPNs, stolen account credentials or security oversights (such as leaving entry points open to the internet).The key thing is that the intrusions were detected and neutralized before a major malicious payload was delivered to the target. It is reasonable to assume that some, if not most, of these intrusions were excess inventory belonging to IABs: “banked” access that had not yet been sold to another adversary. If the intrusions had not been detected it is probable that a significant number would have gone on to become ransomware attacks.
Cryptominers were the main attack type in 2% of the incidents investigated. The presence of malicious cryptominers is often detected through their impact on system performance, as the illicit coin mining draws processing power from computers. It can be tempting to dismiss cryptominers as a lower-level, nuisance threat, but the fact that they are in the network at all proves there is a vulnerable entry point somewhere, and they can be a harbinger of more serious threats to come.The same applies to droppers and malware delivery systems in general, which are designed to deliver, load, or install other malicious payloads to a target system. They are enablers for an unfolding attack, providing a platform for additional malicious modules such as backdoors and ransomware. Defenders therefore need to treat the presence of droppers and malware delivery systems, including Trickbot, Emotet and others, with the same seriousness as a major ransomware group since they are often the precursors to bigger attacks.
A Crowded Playground :
Attack types are not mutually exclusive. As mentioned earlier, multiple adversaries, including IABs, ransomware gangs and cryptominers, can be found in an individual target network at the same time.
For instance, while cryptominers were the main attack type in just 2% of incident response cases, they were also present in 7% of ransomware incidents. Cryptominers often scan for and remove other miners in infected networks but can coexist comfortably with other threats, such as ransomware.
Simultaneous attack incidents reported by Sophos in 2021 include one involving Atom Silo ransomware and two cryptominers, and a dual ransomware attack involving Netwalker and REvil. This trend is continuing into 2022.
The Adversary Toolbox:
Remote Desktop Services are a Major Internal Threat
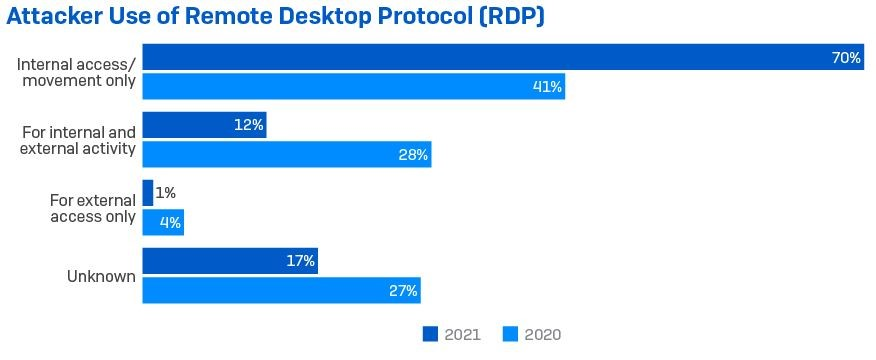
RDP played a part in at least 83% of attacks, an increase from 2020 (when it featured in 73% of attacks). Internal use featured in 82% of cases and external use was seen in 13% of cases. This is against 69% and 32% respectively for 2020.
However, the way in which attackers used RDP is worth noting. In under three quarters (70%) of incidents that involved RDP, the tool was used only for internal access and lateral movement – a significant increase from 41% in 2020.
RDP was used for external access only in just 1% of cases, down from 4% in 2020; and just 12% of attacks showed attackers using RDP for both external access and internal movement, less than half the proportion from 2020 (when it was 28%).
The decline in the use of RDP for external access is likely to reflect improved security, including disabling the service. However, RDP remains widely accessible inside the perimeter, and hardening this access should be a key focus for security teams.
Conclusion:
Every organization is a target for an adversary somewhere, and, increasingly, for more than one. From phishing and financial fraud, to botnet builders, malware delivery platforms, cryptominers, IABs, data theft, corporate espionage, ransomware, and more – if there’s a vulnerable entry point into a network, the chances are that attackers are looking for it and will eventually find and exploit it.
Until the exposed entry point is closed and everything that the attackers have done to establish and retain access is completely eradicated, just about anyone can walk in after them. And probably will. Security teams can defend their organization by monitoring and investigating suspicious activity. The difference between benign and malicious is not always easy to spot. Technology in any environment, whether cyber or physical, can do a great deal, but it is not enough by itself. Human experience, skill, and the ability to respond are a vital parts of any security solution.
The big incident response lessons of 2021 are how quickly and extensively easy-to-exploit, widespread vulnerabilities are seized upon by adversaries, contributing towards longer intrusions and multiple adversaries. For defenders, these lessons mean that detecting, investigating, and responding to the red flags of known adversary toolsets and techniques are more critical than ever.